Norton Antivirus application is a system that protects the computer of yours. It prevents viruses, spyware, Trojan horses, and worms from getting into and causing damage. Norton internet security login performs continuous scans to your computer to safeguard it as you browse sites, download files, and/or open the email. Norton Antivirus is updated automatically and regularly so that your computer stays safe.
Norton Antivirus protects the computer of yours by scanning it always. It immediately blocks anything attempting to get into your computer and asks you to let it enter. If it’s a virus or maybe anything that can potentially result in harm, it isolates it then and immediately alerts you. Norton Antivirus also shields you from becoming infected when you use a quick messaging program. Malicious programs will often attempt to get into your computer in this manner.
Norton additionally blocks phishing attempts from sites that attempt to access personal information like passwords and usernames to many other essential sites, like the bank of yours or maybe the credit card company of yours. It’s automated, and it runs when you switch on the computer of yours.
It blocks against browser and also application threats as well as shields you from infected sites. In case you’re performing some sort of Internet research, you click on a backlink to a different website that happens being afflicted with a disease or maybe something destructive. You will be alerted quickly, which virus will be quarantined and also removed.
Norton Antivirus is accredited by ICSA Labs, a division of Verizon Business. ICSA Labs sets the requirements for the compliance of business protection products. When a business is given the certification, it demonstrates the item has been analyzed independently. A third party has verified the software program does what it really promises (see Resources).
Norton Antivirus Software also got the VB100 Award coming from Virus Bulletin. The Virus Bulletin offers independent testing of antivirus products and also compares them to various other business products.
Once an antivirus software gets this award, it proves it’s been evaluated by a third-bash. VB100 insists that a program show it detects “in the wild” viruses and creates zero false pluses during a scan of unpolluted files.
Some dashing benefits of getting Norton Security:

- This application gives multi-layered security to safeguard you from any possible or even existing threats as stated above
- They also provided free VPN giving use of the web anonymously, consequently protecting your identity, passwords, and private information.
- When the info is utilized for recognition of any specific services, they’ll be notified through Life fastener
- Credit fraud can also be avoided through card monitoring in a software program that reports any illegal activities on yours’s cards.
- In Norton, they supplied four kinds of software types for various customer needs they’re.
- Norton 360 standard format.
- My Norton login center
- Norton 360 with Life Lock established as well as Ultimate Plus.
- All these software programs work with Android, Apple, and windows. They may be downloaded for Pcs, notebooks, mobile phones, and tablets.
This is Automated:
Norton Antivirus is automated, which runs when you switch on the computer of yours. It blocks against browser and also application threats as well as shields you from infected sites. In case you’re performing some sort of Internet research. You click on a backlink to a different website that happens being afflicted with a disease or maybe something destructive. You will be alerted quickly, which virus will be quarantined and also removed.
Awards and also Certifications Norton Antivirus is accredited by ICSA Labs, a division of Verizon Business. ICSA Labs sets the requirements for the compliance of business protection products. When a business is given the certification, it demonstrates the item has been analyzed independently. A third party has verified the software program does what it really promises (see Resources).
Norton Antivirus Software also got the VB100 Award coming from Virus Bulletin. The Virus Bulletin offers independent testing of antivirus products and also compares them to various other business products. Once an antivirus software gets this award, it proves it’s been evaluated by a third-bash. VB100 insists that a program show it detects “in the wild” viruses and creates zero false pluses during a scan of unpolluted files.
Today when you’ve actually fitted the Norton Security, clearly, it needs the activation. Allow me to share the details:
- New customers need to do Norton sign up initially.
- For existing owners that downloaded Norton from Norton.com/setup trigger key element, the unit is triggered instantly if you provided the activation key online.
- For consumers that downloaded through third-party apps should stick to the below procedure
- Norton Log-inis necessary to your Norton the profile of mine to activate the key site and locate the page from the place you downloaded your software upfront.
- If you would like to download it on a new computer system, download the setup once more and install it on yours.
- After setting up, visit the website for activation key
- Click on the My Norton switch next with the Device Security choice.
- To activate the subscription of yours, click activate today in the primary window.
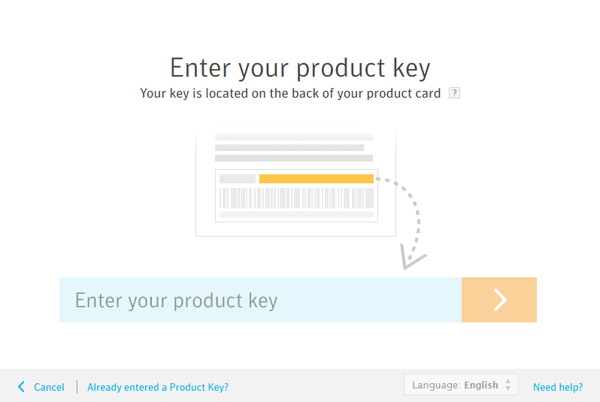
- Now get into your product key or maybe renewal key supplied by Norton.
- Once you get into a valid key element, the program is activated, and also you can begin using Norton instantly.
A few types of malware and virus that an activated edition of Norton can prevent:
Malware may be classified into several different kinds. For instance, the spyware monitors the internet tasks of the infected computer system.
A disease is a kind of malware that spreads by infecting computer applications. Simultaneously, a worm is a kind of virus that replicates by exploiting a vulnerability on a system.
A Trojan horse is a pc program that seems to serve a valuable purpose but hides a virus, hence infecting the pc by tricking the target into a willingly-inforcing it. A rootkit is a virus that can make itself hard to detect by hiding itself through the infected OS.
Virus:

The method that malware makes use of to infect a pc depends on its type. For instance, viruses, Trojan horses, and spyware can infect a computer system once they run or perhaps install the infected system.
Because the infected system carries malware, this particular disease can happen through something downloaded from online or even packed on the computer system from removable media. Some malware can infect a computer system by being downloaded throughout the Web browser whenever the user visits an infected site.
Worms could be especially insidious since they can infect a computer system without the person doing anything. Suppose a hacker discovers a vulnerability in an os. In that case, he can program software that searches for computers on the Internet with which vulnerability and infects them immediately.
Unauthorized Remote Access:
Some kinds of Internet monitoring downloads can also grant online hackers an unauthorized remote entry to your computer. Besides your info being totally exposed, the computer of yours could become a terminal for sending away thousands of spam emails from your email account. This dangerous application can also change your browser’s main page with another, predetermined site.
Adware:

Some spyware, referred to as adware, tracks your web surfing habits, such as internet shopping and discount traveling. Well, then it sends this info to the developers, who focus on the PC of yours with ad pop-ups depending on the collected info, even in case you’re not online.
Malware:

Some malicious Internet monitoring malware, or downloads, could disguise itself as a legitimate anti-spyware software program.
It generates pop-ups to warn you of several spyware threats on your PC. In case you decide to obtain the “anti-spyware,” the computer of yours will solely be precise with increased pop-ups.
It will give warning communications, and the application itself is fake. Several rogue anti-spyware products also start monitoring your Internet pastime upon installation, which will inevitably cause more spyware infection.
Conclusion
Internet monitoring downloads may be downloaded with the consent of yours also. For instance, several legit free application is available in a bundle with spyware. Also, you will need to decide to obtain each in case you want that program.

The key is that this information is generally presented in the “Terms and Conditions” on the download. However, no one is diligent enough to read in the entire point. It is only more comfortable with verifying, “I Agree.”
Some spyware can disguise itself as being an ActiveX Control download. You have to look at websites with animation and also PDF files. You also willingly agree on the download in this situation, thinking you’re setting up antivirus software.
Spyware can control your PC and annoy you with several pop-ups. Still, it can also delay the speed of both the operating system of yours and the Internet connection. Additionally, spyware can alter your registry entries and bring about general computer malfunctions.